Breadcrumb
- Home
- Awareness
- Data types and regulations
- System risk analysis
System Risk Analysis
System Risk Analysis
Per Security Policy (IT-18), Data Stewards are expected to assess institutional risks and threats to the data for which they are responsible. This risk analysis is then used by Data Stewards to classify systems (endpoints, servers, applications) into one of three risk categories:
- Low Risk
- System processes and/or stores public data
- System is easily recoverable and reproducible
- System provides an informational / non-critical service
- Moderate Risk
- System processes and/or stores non-public or internal-use data
- System is internally trusted by other networked systems
- System provides a normal or important service
- High Risk
- System processes and/or stores confidential or restricted data
- System is highly trusted by UI networked systems
- System provides a critical or campus-wide service
Risk Analysis must take into consideration the sensitivity of data processed and stored by the system, as well as the likelihood and impact of potential threat events. We use a simple methodology to translate these probabilities into risk levels and an overall system risk level.
Threat Event Assessment
Risk assessment is the compilation of risks associated with various potential threat events. A "threat event" is any event which may cause a loss of confidentiality, integrity, or availability of the system and the data it stores and/or processes.
Although there may be hundreds of potential threat events related to a system, they can be generally organized into three main categories:
- Loss of Confidentiality:
- The system and its data is compromised by external hackers
- The system and its data is released publicly without approval
- The system and its data erroneously publishes data on public-facing portions of the system (i.e. web page) without authorization
- Loss of Integrity:
- The system and its data can no longer be trusted
- The system and its data is not complete or incorrect
- Loss of Availability:
- The system and its data no longer exists (e.g. hard drive failure, system destroyed)
- The system and its data no longer responds to valid queries from the user or users (system fault)
- The system and its data cannot be retrieved by an authorized user (e.g. Denial of Service Attack)
These threat event categories can then be used to calculate their associated risk level, as well as the overall risk of the system:
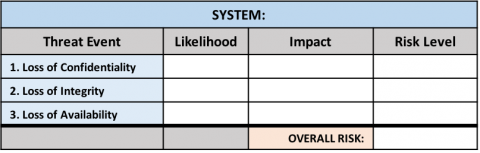
Calculating Risk Levels
Risk levels are calculated as the product of the LIKELIHOOD and IMPACT (to the University) of a potential threat event / threat event category:
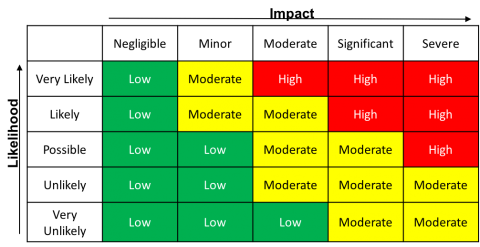
For example, a threat event where the likelihood is "unlikely" and the impact is "moderate" equals an assessed risk of "Moderate":
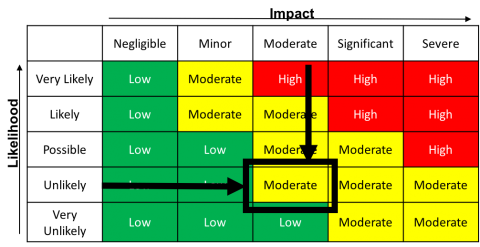
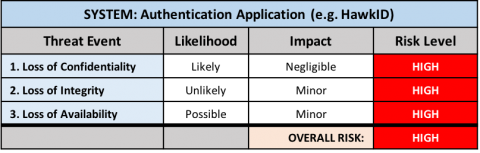
As a general rule, networked systems that process regulated data (e.g. HIPAA, FERPA, FISMA, ITAR, PCI-DSS etc.) are considered high-risk systems. This is because the likelihood of compromise is (at a minimum) possible, while the impact (due to regulatory or industry standard violation) is considered a severe loss of confidentiality.
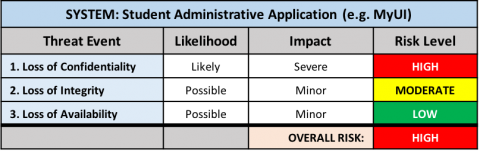
The risk level for each threat event category is then calculated. The overall risk level for the system is equal to the HIGHEST risk level for any risk event. For example:
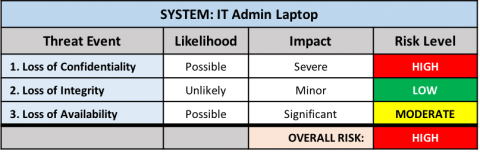
Because one of the risk events was rated as "High Risk", the overall risk level for the system is High.
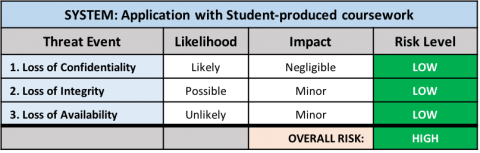
Additional Examples
Endpoints
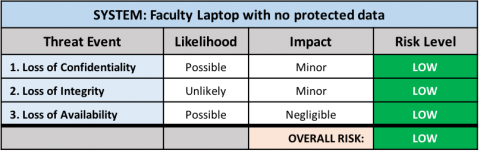
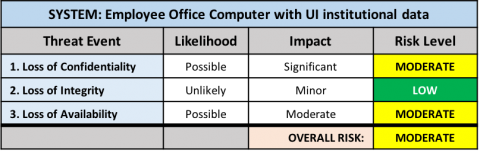
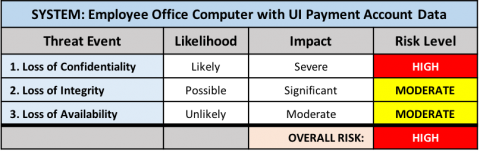
Servers
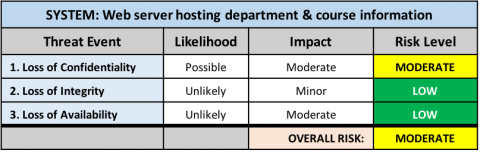
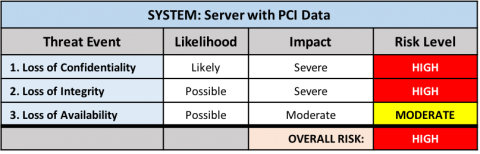
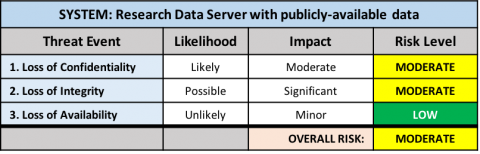
Applications